The submissions for this assignment are posts in the assignment’s discussion. Below are the discussion posts for Richard Bocchinfuso, or you can view the full discussion.
One-off post because Defcon (Links to an external site.)Links to an external site. is happening in Las Vegas, if you wanna see what you’re trying to protect against I suggest the following week’s activities. 🙂 https://twitter.com/hashtag/defcon?src=hash (Links to an external site.)Links to an external site.
From solving fizzbuzz with TensorFlow (Links to an external site.)Links to an external site. to curing cancer (Links to an external site.)Links to an external site. and everything in between machine learning is changing how we programmatically solve problems, no longer focusing on loops, conditionals, and functions to solve a finite problem, but rather using training data and machine learning to teach the computer how to solve problems even if the inputs change from what is expected. Essentially we are using training data to teach the computer to reason, we call this inference. Solving the fizzbuzz problem with TensorFlow is a great example of how machine learning can be used to solve a simple problem.
If you are not familiar with fizzbuzz, it’s a common programmer interview questions.
Write a program that prints the numbers from 1 to 100. But for multiples of three print “Fizz” instead of the number and for the multiples of five print “Buzz”. For numbers which are multiples of both three and five print “FizzBuzz”.
A solution written in python might look like this:

Above you can see the python code solves the problem as presented, but I would have to alter the program to do the same things for a dataset from 101 to 1000. The ridiculous example of using TensorFlow to solve fizzbuzz is the work of Joel Grus and he wrote a hilarious blog (Links to an external site.)Links to an external site. on it. Even though it is a ridiculously complex solution to the problem, and it yields the wrong answer it is a great simple exercise to demonstrate the value of a neural network.
Maybe Elon Musk’s warning that AI could become “an immortal dictator from which we would never escape” is exaggerated for effect and Twitter fame, but it seems that AI will clearly be a strong field general with supreme control over the chosen battlefield. It’s about more than autonomous machines, it’s about autonomous everything, it’s about not solving fizzbuzz with loops and conditional statements, but rather by building a neural network that can solve any variation of fizzbuzz. It’s not about using malware signatures and firewall rules which statically protects north-south and east-west traffic or stateful packet inspection which requires a known signature but rather building a neural network that can continuously train and continuously improve protections, bad news, the hacker community is leveraging machine learning, deep learning and AI to find and exploit vulnerabilities. It’s an arms race and both sides have fully operational uranium enrichment plants, we’ll call them TensorFlow, MXNet, Pytorch and a seemingly endless supply of uranium which we’ll call cloud GPUs. 🙂 Cisco calls this “The Network. Intuitive.” I only use Cisco as an example because they made a fancy commercial that that dramatizes the uses of Machine Learning, Deep Learning and Artificial Intelligence to build what they call “The Network. Intuitive.” Oh, and who doesn’t love Tyrion Lannister?
Discussion: Identify requirements that should be considered when determining the locations and features of firewalls. What are some important steps to take to keep firewalls effective?
In the context of “determining the locations and features of firewalls,” I believe it is critical to understand how infrastructure and traffic patterns are evolving. Firewalls have always been essential in filtering and protecting north-south network traffic. The emergence of technologies like virtualization and software-defined networking (SDN) has dramatically increased east-west network traffic. Like long-range ballistic missiles have impacted aspects of the layer one protection provided by the oceans, these technologies have negated aspects of the physical layer one protection provided by physical network segmentation. Technologies like virtualization and SDN have accelerated the development of next-generation firewalls (NGFW) that deliver a “deep-packet inspection firewall that moves beyond port/protocol inspection and blocking to add application-level inspection, intrusion prevention, and bringing intelligence from outside the firewall.” (Aldorisio, 2017)

Most people are reasonably familiar with perimeter security best practice.
A model that many people are familiar with is the bastion host topology. The bastion host topology would be the type firewall topology deployed on most home networks where the LAN (Intranet) and WAN (Internet) are firewalled by a cable modem which acts as the router and firewall.

A more complex network may utilize a screened subnet topology the implementation of a DMZ (Demilitarized Zone). In the screened subnet topology, systems that host public services are placed on the DMZ subnet rather than on the LAN subnet. The screened subnet topology separates public services from the LAN or trusted subnet by locating publically accessible services in the DMZ. This approach adds a layer of protection so that if a publically available service becomes compromised, there is an added layer of security aimed at stopping an attacker from traversing from the DMZ subnet to the LAN subnet.
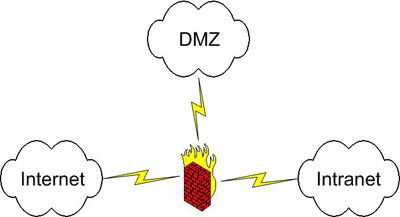
A topology which takes the screened subnet a step further is a dual firewall topology where the DMZ (Demilitarized Zone) is placed between two firewalls. The dual firewall topology is a common topology implemented by networking security professional, often using firewalls from different providers as an added layer of protection should an attacker identify and exploit a vulnerability in a vendors software.
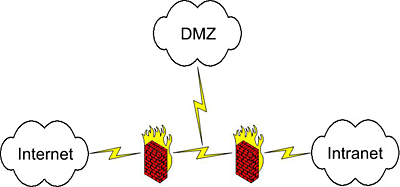
Enterprise-grade firewalls also allow for more complex topologies which extend the topologies described above beyond internal (LAN), external (WAN) and DMZ networks. Enterprise-grade firewalls support more interfaces, faster processors which allow more layered intelligent services, higher throughput, etc. The support of software features such as virtual interfaces, VLANs, VLAN tagging, etc. allows for greater network segmentation enabling the ideas discussed above to be applied discretely based on requirements.
Some steps to maintain firewall effectiveness include (Mohan, 2013):
- Clearly defining a firewall change management plan
- Test the impact of firewall policy changes
- Clean up and optimize firewall rule base
- Schedule regular firewall security audits
- Monitor user access to firewalls and control who can modify firewall configuration
- Update firewall software regularly
- Centralize firewall management for multi-vendor firewalls
References
Aldorisio, J. (2017, November 27). What is a Next Generation Firewall? Learn about the differences between NGFW and traditional firewalls. Retrieved August 17, 2018, from https://digitalguardian.com/blog/what-next-generation-firewall-learn-about-differences-between-ngfw-and-traditional-firewalls
Chapple, M. (2018, August 17). Choosing the right firewall topology: Bastion host, screened subnet or dual firewalls. Retrieved August 17, 2018, from https://searchsecurity.techtarget.com/tip/Choosing-the-right-firewall-topology-Bastion-host-screened-subnet-or-dual-firewalls
Ergun, O. (2015, January 10). What is East-West and North-South Traffic | Datacenter Design. Retrieved August 17, 2018, from https://orhanergun.net/2015/01/east-west-north-south-traffic/
Hossain, M. (2014, May 21). Trends in Data Center Security: Part 1 – Traffic Trends. Retrieved August 17, 2018, from https://blogs.cisco.com/security/trends-in-data-center-security-part-1-traffic-trends
How Does Micro-Segmentation Help Security? Explanation. (n.d.). Retrieved August 17, 2018, from https://www.sdxcentral.com/sdn/network-virtualization/definitions/how-does-micro-segmentation-help-security-explanation/
Mohan, V. (2013). Best Practice for Effective Firewall Management. Retrieved August 17, 2018, from http://cdn.swcdn.net/creative/v9.3/pdf/Whitepapers/Best_Practices_for_Effective_Firewall_Management.pdf
Network and Traffic Segmentation. (n.d.). Retrieved August 17, 2018, from https://www.pluribusnetworks.com/solutions/network-traffic-segmentation/
Scott, good post. Question: Do you think that it will be possible to compete in the enterprise NGFW market without a cloud-based model? My contention is that the aggregation and profiling of data gathered from deep packet inspection across the entire the industry will allow NGFW OEMs to better identify and address threats. These datasets will also function as training data for machine learning, deep learning and AI models. My belief is that the cloud is and will continue to play a huge role in the innovation and adoption of NGFW technologies.
